What Is HashiCorp Vault?
HashiCorp Cloud Platform (HCP) Vault is a tool for secrets management, offering secure access to tokens, passwords, certificates, API keys, and other sensitive resources. It centralizes and encrypts sensitive assets to manage and control access, supporting rigorous security measures across dynamic cloud infrastructure.
Developed by HashiCorp, Vault can tightly control access to secrets, enforce policies, and record detailed audit logs. This functionality enhances security and compliance within organizations. Its dynamic secrets feature offers unique credentials, which can be automatically rotated and revoked, significantly reducing the potential for unauthorized access.
HashiCorp Vault was originally offered as an open source product, with additional features as part of a paid subscription. However, in late 2023 the company transitioned the product to a Business Source License (BSL), which allows free use with some limitations.
In this article:
HashiCorp Vault Key Features
Here are some of the main features of Vault.
1. Identity-Based Security
HashiCorp Vault’s identity-based security model allows it to authenticate and authorize access to secrets based on verified identities. This model employs various authentication methods such as tokens, usernames and passwords, multi-factor authentication, and certificates to verify the identity of clients requesting access to the secret store. Once authenticated, Vault assigns policies to these identities, which define what actions the identities are permitted to perform.
The security model integrates with external identity providers like Active Directory, LDAP, and cloud identity services. This integration allows Vault to leverage existing organizational identities and group memberships to manage access to secrets. This makes it easier to implement consistent security policies across a company’s infrastructure.
2. Secrets Management
In HashiCorp Vault, secrets management is designed to handle various types of sensitive data including passwords, certificates, and API keys. Vault secures these secrets by encrypting them before they are stored. This ensures that all sensitive information remains protected both at rest and in transit.
The tool supports dynamic secrets, which are generated on the fly and can be automatically expired or revoked when no longer needed. This capability reduces the risks associated with static credentials that can be exposed or mishandled.
Vault’s secrets management capability also includes versioning of secrets, which allows users to roll back to previous versions if needed. This feature is particularly useful in managing configurations and handling secret rotations without service interruptions. Vault’s API facilitates seamless integration with existing applications and systems, enabling automated secrets management processes.
3. Keys Management
HashiCorp Vault’s keys management functionality involves the secure storage, generation, and handling of cryptographic keys. Vault can generate new keys, encrypt and decrypt data, sign and verify signatures, all while ensuring that cryptographic keys are never exposed to clients or stored unencrypted. It supports various types of keys including symmetric, asymmetric, and HMAC keys, providing flexible options for different security requirements.
Vault’s keys management capabilities include automatic key rolling, which helps maintain security by regularly updating keys and limiting their lifespan. This prevents the long-term use of a single key that could potentially be compromised. Vault also provides detailed audit logs for key usage, which is critical for compliance and security monitoring. These logs record every operation performed with the keys, offering visibility and traceability.
4. Certificates Management
Vault’s certificates management system automates the process of creating, distributing, and renewing TLS/SSL certificates. This system reduces the complexity and administrative burden associated with managing large numbers of certificates, which is common in large-scale and dynamic environments. By automating these tasks, Vault helps ensure that certificates are issued correctly and renewed before they expire.
The tool also supports a Certificate Authority (CA) integration, which allows Vault to issue certificates on behalf of an organization’s CA. This makes it possible to maintain a private trust model while leveraging Vault’s automation capabilities. Vault can also handle multiple CAs, enabling organizations to manage different levels of trust within their environments.
5. Integration with Identity Providers
HashiCorp Vault integrates seamlessly with multiple identity providers (IdPs), enabling organizations to enforce their existing user authentication and authorization mechanisms within Vault. This integration supports IdPs like Active Directory, LDAP, OAuth, and cloud-native identity services, allowing Vault to leverage an organization’s current identity management infrastructure.
This integration also extends to the configuration of single sign-on (SSO) systems, enabling users to authenticate with Vault using the same credentials they use across other systems. Vault’s integration with identity providers simplifies the management of complex identities and reduces the potential for security breaches by centralizing user authentication and authorization.
Related content: The GitOps Guide
HashiCorp Vault vs. Consul
Despite both being HashiCorp products, Vault and Consul serve distinct purposes. They integrate seamlessly, addressing different aspects of infrastructure management and security.
Vault specializes in secrets management, ensuring secure storage, and access to sensitive information. Its primary focus is safeguarding secrets and enabling fine-grained access control.
Consul provides service discovery and configuration. It enables services to discover each other in dynamic infrastructure environments and securely configure themselves.
Tips From the Expert
In my experience, here are tips that can help you better leverage HashiCorp Vault for secrets management:
-
Use dynamic secrets for enhanced security Take full advantage of Vault’s dynamic secrets feature, which generates ephemeral credentials on-demand and automatically revokes them after use. This minimizes the risk of long-lived static secrets being compromised, reducing your attack surface.
-
Segment Vault namespaces for multi-team environments When managing secrets for different teams or departments, use Vault’s namespace feature to isolate secrets and policies for each team. This allows fine-grained access control and better organization in large-scale infrastructures.
-
Automate secret rotation and lifecycle management Ensure all sensitive secrets, especially database credentials and API keys, are automatically rotated at regular intervals. Vault supports automated rotation, which should be configured to enforce strong security practices without requiring manual intervention.
-
Monitor and alert on anomalies in secret access Integrate Vault with SIEM (Security Information and Event Management) systems to monitor access logs and set up alerts for suspicious behavior. This enables proactive detection of unauthorized access attempts or anomalous activity related to secrets.
-
Integrate Vault with cloud-native and external identity providers Leverage Vault’s integration with cloud identity services (e.g., AWS IAM, GCP, Azure AD) and external providers (LDAP, OAuth) to enforce consistent authentication mechanisms. This simplifies secret access across hybrid environments while maintaining security compliance.
How HashiCorp Vault Works
Here’s an overview of the Vault workflow.
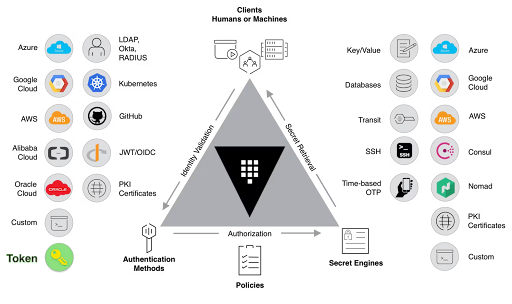
1. Authentication
A client provides specific information to Vault, enabling it to verify the client’s identity. This process is essential for ensuring that the interaction with Vault begins with a confirmation of the client’s claimed identity. Upon successful authentication, Vault generates a token. This token is directly linked to a policy that outlines the permissions and access rights of the client, serving as a key for subsequent operations within Vault.
2. Validation
After authentication, Vault proceeds to validate the client against trusted third-party sources. These sources can include systems and services such as Github, LDAP, and AppRole. This validation process is crucial for ensuring the authenticity of the client and aligning their access capabilities with external verification mechanisms.
3. Authorization
During the authorization stage, the client is matched against the security policies established within Vault. These policies are sets of rules that define what actions the client is permitted to perform within Vault, specifying which API endpoints they can access with their Vault token. Policies in Vault are declarative, granting or restricting access to various paths and operations.
4. Access
In the final stage of the Vault workflow, access is granted to the client based on the policies associated with their identity. Vault issues a token to the client, which embodies these policies and outlines the scope of operations and resources the client is authorized to utilize. With this token, the client can access Vault’s secrets, keys, and encryption capabilities.
Learn more in our detailed guide about HashiCorp Vault Docker
HashiCorp Vault Pricing
Let’s look at the pricing model for Vault.
HCP Vault Secrets
Vault allows individual developers or small teams beginning to explore secrets management solutions free access to 25 secrets per month.
There is a free tier that supports up to 25 applications and 25 secrets, compared to the Standard tier that supports 1000 applications and 2500 secrets, with each secret priced at $0.50 per month. There is no credit card requirement to start using this service.
HCP Vault
For those requiring a more dedicated solution, the HCP Vault service starts at $1.58 per hour. HCP Vault offers dedicated clusters in Development, Standard, and Plus tiers, available on a pay-as-you-go basis or under an annual subscription (for the Standard and Plus tiers).
This managed option provides a dedicated cloud instance designed for identity-based security, facilitating the management and protection of access to secrets and sensitive data. Enterprise support is included in this tier.
Enterprise Custom
The Enterprise Custom plan is the most advanced and adaptable offering from HashiCorp. It’s intended for large enterprises with specific security, compliance, and operational requirements that go beyond standard offerings.
This self-managed solution allows for customization to meet complex needs and includes enterprise support. Pricing is available upon request from HashiCorp.
Learn more in our comprehensive guide to HashiCorp Vault Pricing.
Best HashiCorp Vault Alternatives
While HashiCorp Vault is a respected secrets management solution, there are several alternative solutions worth considering. Here are a few popular Vault alternatives.
Configu
Configu is the most innovative store purpose-built for configurations, including environment variables, secrets, and feature flags. It is built based on the Configu configuration-as-code (CaC) approach and can model configurations and wrap them with unique layers, providing collaboration capabilities, visibility into configuration workflows, and security and compliance standardization.
Unlike legacy tools, which treat configurations as unstructured data or key-value pairs, Configu is leading the way with a Configuration-as-Code approach. By modeling configurations, they are treated as first-class citizens in the developers’ code. This makes our solution more robust and reliable and also enables Configu to provide more capabilities, such as visualization, a testing framework, and security abilities.
Learn more about Configu for secrets management
Cyberark Conjur
CyberArk Conjur is a centralized secrets management solution designed to address common challenges in securing, rotating, and managing secrets sprawled across various applications, vaults, tools, and source code.
By centralizing secrets management, Conjur aims to streamline application development processes, ensuring secure access control across tools, applications, and cloud environments. This overcomes secrets sprawl, mitigates the risk associated with a single master key, and breaks down silos between security policies and audit data.
Key features of CyberArk Conjur:
- Centralized secrets management: By centralizing secrets management, it simplifies the application development lifecycle and enhances security.
- Secretless broker: Offers simplified security within Kubernetes and Red Hat OpenShift environments by enabling applications to connect to services without needing to manage secrets.
- Secrets management REST API: Allows for easy integration with tools like Postman for managing secrets.
- AWS IAM authenticator: Supports authentication of access requests to Conjur using AWS IAM, ensuring secure and streamlined access control.
- Java secrets management SDK: A dedicated SDK for securing Java applications through the Conjur Java API, facilitating secure application development and integration.
Source: CyberArk
AWS Secrets Manager
AWS Secrets Manager is a service designed to manage the lifecycle of secrets such as database credentials, API keys, and other sensitive information. It enables secure encryption and centralized auditing of secrets, alongside fine-grained access management using AWS Identity and Access Management (IAM) and resource-based policies.
Secrets Manager simplifies the process of rotating secrets to adhere to security and compliance guidelines and supports the replication of secrets for disaster recovery and multi-region applications. It integrates with other AWS services, ensuring a secure storage, access, rotation, and monitoring framework for secrets.
Key features of AWS Secrets Manager:
- Secure secrets storage: Secrets are encrypted at rest using keys from AWS Key Management Service (AWS KMS), ensuring robust security. When retrieved, secrets are decrypted and transmitted securely over TLS, with access controlled by detailed IAM and resource-based policies.
- Automatic secrets rotation: Enables automatic rotation of secrets either on-demand or on a scheduled basis, without disrupting application performance. It supports native rotation for Amazon RDS, Amazon DocumentDB, and Amazon Redshift credentials.
- Automatic replication across AWS regions: To meet disaster recovery and cross-regional redundancy requirements, Secrets Manager can replicate secrets to multiple AWS Regions automatically. This feature creates regional read replicas of secrets, simplifying the management of multi-region applications.
- Audit and monitor secrets usage: Integrates with AWS logging, monitoring, and notification services, expanding the auditing and monitoring of secrets. It allows for auditing secret creation and rotation via AWS CloudTrail logs and configuring Amazon CloudWatch for notifications on secrets usage or rotation events.
Source: Amazon
Azure Key Vault
Azure Key Vault offers a secure, streamlined way to manage cryptographic keys and other secrets like passwords, used by cloud applications and services. It emphasizes enhancing data protection and compliance through the encryption of keys and small secrets using hardware security modules (HSMs).
Key Vault supports the import and generation of keys within HSMs that are validated to FIPS 140-2 Level 2 for vaults and Level 3 for HSM pools. The service is designed to provide users with control over their keys while eliminating the complexity of managing the underlying infrastructure.
Key features of Azure Key Vault:
- Security and control: Aims to increase security and control over cryptographic keys and passwords, using FIPS 140-2 Level 2 and Level 3 validated HSMs for key encryption and management.
- Simplified management: Eliminates the need for direct application access to keys, streamlines the management of SSL/TLS certificate tasks, and supports the importation of keys from user-owned HSMs.
- Reduced latency and global scale: Scales quickly to meet the cryptographic demands of applications and supports provisioning in Azure global datacenters for enhanced redundancy.
- Automated tasks for SSL/TLS certificates: Simplifies and automates the enrollment and renewal of certificates from supported public Certificate Authorities, allowing for seamless certificate management.
Source: Azure
Conclusion
HashiCorp Vault is a powerful tool for secrets management. With its capabilities in identity-based security, dynamic secrets management, and integration with various identity providers, Vault provides a solid foundation for protecting sensitive information.
However, alternatives like Configu, CyberArk Conjur, AWS Secrets Manager, and Azure Key Vault also offer compelling features that might be better suited for specific organizational requirements or technical environments. Choosing the right secrets management tool depends on factors such as specific security needs, scalability requirements, and the existing technological ecosystem of an organization.



