What Is HashiCorp Consul?
HashiCorp Consul is an open source, multi-cloud service networking tool that enables automated network configuration and service discovery. It provides a reliable and scalable way to connect and secure services across any runtime platform and public or private cloud. Its capabilities include service discovery, health checking, and a key/value store.
Consul simplifies complex networking by allowing users to discover services and securely manage connections between them with automated TLS encryption and identity-based authorization. It helps reduce the manual effort required for network administrators to manage dynamic infrastructure.
This is part of a series of articles about HashiCorp Vault
In this article:
How Consul Works: Understanding the Architecture
Here is an overview of the main components of the HashiCorp Consul architecture.
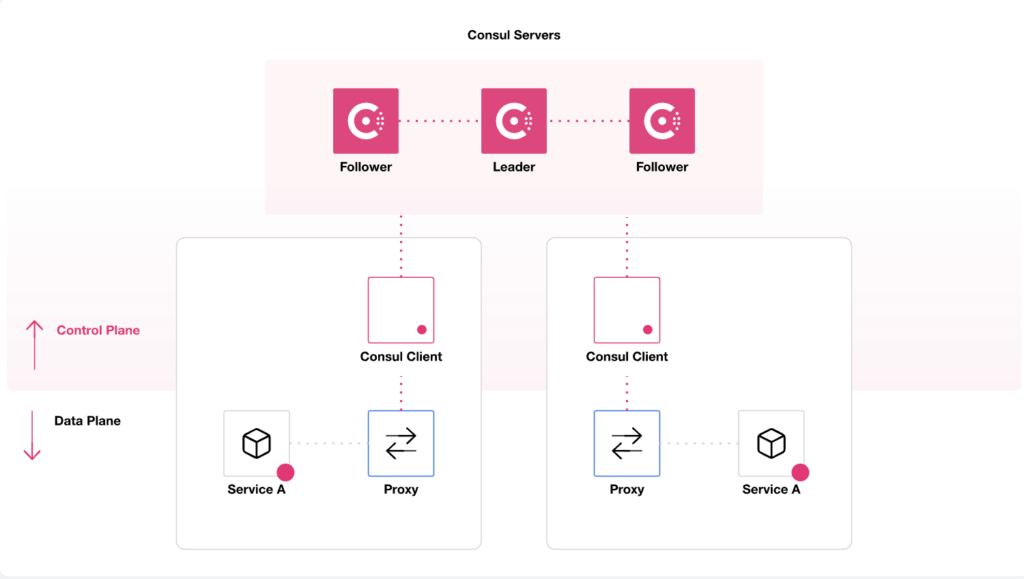
Related content: The GitOps Guide
Datacenters
A datacenter is the highest deployment unit in Consul, typically encompassing services within a single physical datacenter or cloud region. Services within the same datacenter can communicate with low latency. Consul ensures that all members within a datacenter are identical, and members can take over tasks from each other for high availability.
The ability to span multiple datacenters enables secure service communication across geographical locations. This design promotes scalability and resilience, ensuring that even if one datacenter fails, services can fallback to another without significant disruption.
Clusters
A cluster in Consul is a group of nodes hosting services that are managed together. Each cluster has a set of server nodes, which are responsible for managing the state of the cluster, and client nodes, which run services and report their status back to the server nodes. The cluster is the primary unit of scalability and resilience in Consul.
Clusters are designed to handle failures gracefully. If a server node fails, other server nodes in the cluster take over its responsibilities without impacting service discovery or networking capabilities. This ensures uninterrupted service operations and maintains system stability.
Agents
Agents are the core components running on every node in the Consul cluster, acting as bridges between services and the Consul ecosystem. They perform critical functions such as health checking, service registration, and configuration. Each agent has a local cache, improving data retrieval performance and reducing load on the Consul servers.
Besides basic operations, agents support various modes, primarily server and client, determining their role within the architecture. Server agents participate in the consensus protocol and store state information, while client agents forward queries to servers and manage local services.
LAN Gossip Pools
The LAN gossip pool enables near-real-time updates across the cluster. Using a gossip protocol, nodes share information in a consistent and scalable manner. This facilitates dynamic service discovery and configuration updates without significant network overhead.
This gossip mechanism ensures that updates about service registrations, health status changes, and more are propagated quickly and accurately across all nodes in the same datacenter. This supports a resilient and responsive network.
WAN Gossip Pools
Consul can handle cross-datacenter requests, enabling services in different datacenters to communicate securely and efficiently. Through built-in support for WAN gossip pools and gateways, Consul automates the routing and resolution of cross-datacenter service requests, abstracting the complexity of multi-region deployments.
WAN gossip pools extend the LAN gossip’s functionalities, ensuring seamless service discovery and connectivity across datacenters. Consul’s intelligent routing and secure communication channels mitigate latency and security challenges in distributed setups.
Common Use Cases for Consul
HashiCorp Consul is often used for the following purposes.
Network Infrastructure Automation
Consul automates network configurations, reducing manual intervention and facilitating agile infrastructure management. It dynamically updates the network as services change, aligning with the principles of Infrastructure as Code (IaC). This automation extends across multiple platforms and environments, improving operational efficiency and consistency.
The tool integrates with existing DevOps practices, offering APIs and tools that simplify integrating networking into CI/CD pipelines. This allows teams to deploy and manage their services more rapidly.
Access Control
Consul provides mechanisms to control access to services, enhancing security and compliance. By leveraging identity-based policies, organizations can define precise access controls, ensuring that only authorized entities can interact with sensitive services. This aids in maintaining data security and privacy.
Access control in Consul is fine-grained, allowing administrators to specify policies at the service level. This enables tailored security postures, from broad open access to strict, need-to-know access, based on the organization’s requirements and regulatory obligations.
Multi-Platform Service Mesh
Consul’s service mesh capabilities enable unified, cross-platform service communication within diverse environments. It abstracts the complexity of inter-service communications, providing a consistent, centralized way to connect, manage, and secure services across multiple runtimes and clouds.
This approach supports hybrid and multi-cloud strategies. The service mesh simplifies networking by automating service discovery, encryption, and configuration.
Zero Trust Networking
In a zero trust approach, no entity is trusted by default, regardless of its network or location. Consul enforces zero trust networking by requiring all communication to be authenticated and authorized. It leverages mutual TLS (mTLS) for encrypted, authenticated connections, ensuring that only verified services can communicate.
Implementing zero trust with Consul enhances the organization’s security posture, reducing the attack surface and minimizing the risk of data breaches. This is especially important in a distributed environment where the traditional network perimeter no longer exists.
Tips From the Expert
In my experience, here are tips that can help you better deploy and optimize HashiCorp Consul:
-
Optimize agent performance with caching
Utilize Consul’s built-in agent caching for services, key/value store data, and health checks. Caching reduces the need for constant server queries, improving response times and reducing load on Consul servers in large-scale environments. -
Integrate service discovery with external systems
To extend Consul’s service discovery, integrate it with external tools such as Kubernetes or AWS CloudMap. This expands the range of services Consul can monitor and interact with, making it adaptable to hybrid architectures. -
Utilize Consul’s Prepared Queries for custom service logic
Prepared queries allow for advanced service discovery logic, including service failover or latency-based routing. Leverage these queries to build more resilient service discovery mechanisms that can adapt to dynamic infrastructure changes. -
Leverage Consul Connect for secure service communication
Consul Connect provides native support for service-to-service encryption and authentication using mutual TLS (mTLS). This can be particularly effective for zero-trust networking and preventing unauthorized services from communicating with each other. -
Monitor with Consul’s telemetry data
Use Consul’s telemetry data to monitor cluster health, performance metrics, and service failures. Integrating these metrics with tools like Prometheus and Grafana gives you insights into bottlenecks and potential failures early on.
Deployment Guidelines for HashiCorp Consul
Here are guidelines for deploying HashiCorp Consul, based on the official Consul reference architecture.
Ensure Appropriate Hardware Capacity
For successful deployment and operation of HashiCorp Consul, it’s critical to begin with the right hardware capacity:
- Small clusters, suitable for initial production deployments or development environments, should have 2-4 CPU cores, 8-16 GB of RAM, and disks capable of 3000+ IOPS and 75+ MB/s throughput.
- Large clusters, designed for high workload production environments, require significantly more robust hardware: 8-16 CPU cores, 32-64 GB of RAM, with disks supporting 7500+ IOPS and 250+ MB/s throughput.
Secure Network Communications with Consul Agents
Securing communication within the Consul cluster is essential for maintaining data integrity and privacy. Implementing Access Control Lists (ACLs) provides authentication and authorization for accessing Consul resources.
Additionally, configuring symmetric encryption for the gossip protocol and utilizing TLS for HTTP, RPC, and gRPC protocols encryption and authentication are critical measures. In service mesh scenarios, mutual TLS (mTLS) facilitated by sidecar proxies ensures encrypted and authenticated service-to-service communication, further bolstering the security posture of your Consul deployment.
Scale the Datacenter Appropriately
The maximum recommended size for a single datacenter is around 5,000 client agents, a limit influenced not just by scalability but also by the potential impact and recovery considerations of a datacenter failure.
Key factors affecting the scalability include the size of the gossip pool, the rate of agent joins/leaves, and the volume of managed services. Monitoring these factors closely and adjusting the deployment as necessary can help ensure stable and efficient operation of the Consul cluster.
Consider Fault Tolerance
Designing for fault tolerance involves planning for various failure scenarios, including node, availability zone, and even entire region failures. A resilient Consul architecture should allow for the loss of nodes or an availability zone without compromising the cluster’s functionality.
For enhanced failure tolerance, especially in larger deployments, leveraging features like redundancy zones and non-voting server agents in Consul Enterprise can offer additional layers of stability and resilience.
Read more about related topics:
Secret Management with Configu
Configu is a configuration management platform comprised of two main components:
Configu Orchestrator
As applications become more dynamic and distributed in microservices architectures, configurations are getting more fragmented. They are saved as raw text that is spread across multiple stores, databases, files, git repositories, and third-party tools (a typical company will have five to ten different stores).
The Configu Orchestrator, which is open-source software, is a powerful standalone tool designed to address this challenge by providing configuration orchestration along with Configuration-as-Code (CaC) approach.
Configu Cloud
Configu Cloud is the most innovative store purpose-built for configurations, including environment variables, secrets, and feature flags. It is built based on the Configu configuration-as-code (CaC) approach and can model configurations and wrap them with unique layers, providing collaboration capabilities, visibility into configuration workflows, and security and compliance standardization.
Unlike legacy tools, which treat configurations as unstructured data or key-value pairs, Configu is leading the way with a Configuration-as-Code approach. By modeling configurations, they are treated as first-class citizens in the developers’ code. This makes our solution more robust and reliable and also enables Configu to provide more capabilities, such as visualization, a testing framework, and security abilities.



